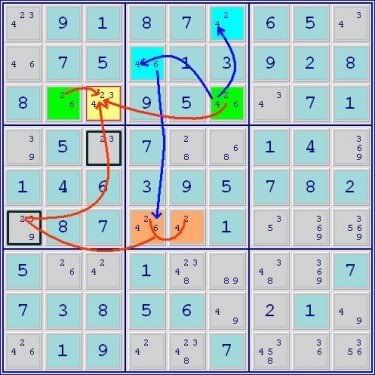
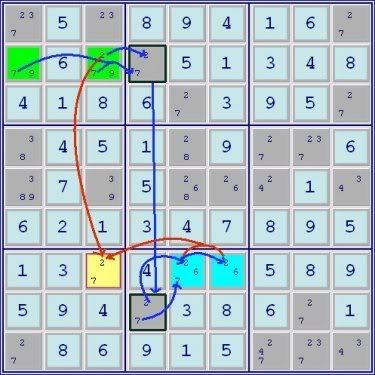
ronk wrote:Aha, I see some trickery here with the naked pair between the two ALSs. I'll have to study that a bit more....
Seven cover sets are required for the six cells. In a true ALS doubly-linked xz-rule, the number of base sets and cover sets would be equal. Since the ALSs are not doubly-linked, if follows that there is no corresponding "restricted common elimination" either.
This appears to be a rather interesting situation where, on the surface, the description is accurate, but in the end, the example fails. Since this is meant to be accessible particularly to newer solvers, I think there is another way of looking at the problem that can be described without using base sets & cover sets which the less experienced wouldn't understand.
First, the standard restricted common definition: A digit is restricted common to 2 Almost Locked Sets when it cannot be present in both sets at the same time. In the example in question, taken separately, the 2 and the 7, through the direct conjugate links, appear to fulfill that definition. Thus, it would appear that 2 ALSs+2 restricted commons = doubly linked, but the resolution of the pattern doesn't end up working that way. The problem is that, probably unique to this type of example, the resolution of either of the restricted common links destroys the other or put another way satisfying one of the restricted commons solves for the naked pair destroying both conjugate pairs.
If this perspective is correct, maybe there needs to be some small print added to the doubly linked ALS definition that the restricted commons have to operate independently of each other or something to that effect. So, since I like to keep things simple, it appears that the 'double' conjugate link doesn't work; the base/cover set explanation likely uncovers the underlying flaw in the logic. In any event, thanks for pointing out that the example is flawed. This tutorial has to be as accurate as reasonably possible so the graphic will be replaced.